参考”2-5”
K8S的各个组件之间是通过tls加密进行通讯的。
既然要加密,就要用到数字证书。
这里把集群中要用到的所有证书都封装好,以便后续的使用。
#提示:下述内容记得脱敏!
安装cfssl
#只在node-1节点下载
#cfssl是非常好用的CA工具,我们用它来生成证书和秘钥文件 安装过程比较简单,如下:
# 下载
[root@node-1 ~]# wget https://pkg.cfssl.org/R1.2/cfssl_linux-amd64 -O /usr/local/bin/cfssl
[root@node-1 ~]# wget https://pkg.cfssl.org/R1.2/cfssljson_linux-amd64 -O /usr/local/bin/cfssljson
# 修改为可执行权限
[root@node-1 ~]# chmod +x /usr/local/bin/cfssl /usr/local/bin/cfssljson
[root@node-1 ~]# ll /usr/local/bin/cfssl*
-rwxr-xr-x 1 root root 10376657 Dec 7 2021 /usr/local/bin/cfssl
-rwxr-xr-x 1 root root 2277873 Dec 7 2021 /usr/local/bin/cfssljson
# 验证
[root@node-1 ~]# cfssl version
Version: 1.2.0
Revision: dev
Runtime: go1.6
根证书
#根证书是集群所有节点共享的,只需要创建一个根证书CA证书,后续创建的所有证书都由这个根证书CA签名/签发的。
在任意节点(可以免密登录到其他节点)创建一个单独的证书目录,如:mkdir pki && cd pki(所有的证书都放在这个文件夹中)
应该在/root/pki中。
#根证书配置文件
[root@node-1 ~]# mkdir pki && cd pki
#这里把CA证书的过期时间已经调整的非常长了,后面就不用考虑过期问题了。
[root@node-1 pki]# cat > ca-config.json <<EOF
{
"signing": {
"default": {
"expiry": "876000h"
},
"profiles": {
"kubernetes": {
"usages": ["signing", "key encipherment", "server auth", "client auth"],
"expiry": "876000h"
}
}
}
}
EOF
[root@node-1 pki]# cat > ca-csr.json <<EOF
{
"CN": "Kubernetes",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "US",
"L": "Portland",
"O": "Kubernetes",
"OU": "CA",
"ST": "Oregon"
}
]
}
EOF
[root@node-1 pki]# ll
total 8
-rw-r--r-- 1 root root 236 Nov 3 15:01 ca-config.json
-rw-r--r-- 1 root root 211 Nov 3 15:01 ca-csr.json
#生成证书和私钥
#生成的根证书CA是先开始的
[root@node-1 pki]# cfssl gencert -initca ca-csr.json | cfssljson -bare ca
2022/11/03 15:02:18 [INFO] generating a new CA key and certificate from CSR
2022/11/03 15:02:18 [INFO] generate received request
2022/11/03 15:02:18 [INFO] received CSR
2022/11/03 15:02:18 [INFO] generating key: rsa-2048
2022/11/03 15:02:18 [INFO] encoded CSR
2022/11/03 15:02:18 [INFO] signed certificate with serial number XX
# 生成完成后会有以下文件(我们最终想要的就是ca-key.pem和ca.pem,一个秘钥,一个证书)
[root@node-1 pki]# ll
total 20
-rw-r--r-- 1 root root 236 Nov 3 15:01 ca-config.json
-rw-r--r-- 1 root root 1005 Nov 3 15:02 ca.csr
-rw-r--r-- 1 root root 211 Nov 3 15:01 ca-csr.json
-rw------- 1 root root 1679 Nov 3 15:02 ca-key.pem
-rw-r--r-- 1 root root 1367 Nov 3 15:02 ca.pem
组件证书:admin客户端证书 (kubectl)
#比如kubectl就会用到此证书。管理员生成admin的配置文件,根据根证书签发的配置文件。
#admin客户端证书配置文件
[root@node-1 pki]# cat > admin-csr.json <<EOF
{
"CN": "admin",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "BeiJing",
"L": "BeiJing",
"O": "system:masters",
"OU": "seven"
}
]
}
EOF
#生成admin客户端证书和私钥
#是由刚才生成的根证书CA去签发的证书文件
[root@node-1 pki]# cfssl gencert \
-ca=ca.pem \
-ca-key=ca-key.pem \
-config=ca-config.json \
-profile=kubernetes \
admin-csr.json | cfssljson -bare admin
2022/11/03 15:11:29 [INFO] generate received request
2022/11/03 15:11:29 [INFO] received CSR
2022/11/03 15:11:29 [INFO] generating key: rsa-2048
2022/11/03 15:11:29 [INFO] encoded CSR
2022/11/03 15:11:29 [INFO] signed certificate with serial number XX
2022/11/03 15:11:29 [WARNING] This certificate lacks a "hosts" field. This makes it unsuitable for
websites. For more information see the Baseline Requirements for the Issuance and Management
of Publicly-Trusted Certificates, v.1.1.6, from the CA/Browser Forum (https://cabforum.org);
specifically, section 10.2.3 ("Information Requirements").
[root@node-1 pki]# ll admin*
-rw-r--r-- 1 root root 1009 Nov 3 15:11 admin.csr
-rw-r--r-- 1 root root 213 Nov 3 15:11 admin-csr.json
-rw------- 1 root root 1679 Nov 3 15:11 admin-key.pem
-rw-r--r-- 1 root root 1407 Nov 3 15:11 admin.pem
组件证书:kubelet客户端证书
#Kubernetes使用一种称为Node Authorizer的专用授权模式来授权Kubelets发出的API请求。
(Kubernetes去认证kubelet的时候,使用一种称为Node Authorizer的专用授权模式来对Kubelets发出的API请求进行授权。)
Kubelet使用将其标识为system:nodes组中的凭据,其用户名为system:node:nodeName,接下里就给每个工作节点生成证书。
(组后面必须把主机名nodeName,加到最后面去,这种模式就要求每一个kubelets证书都是不一样的,因为每个节点的nodeName都是不同的,
这种模式会让每个worker节点的证书的IP或主机名发生改变,可能就没办法去使用了,这也就更加的保证了集群的安全性。)
#生成kubelet客户端证书和私钥
# 设置你的worker节点列表(定义每个worker节点的名字,在node-1设置)
[root@node-1 pki]# WORKERS=(node-2 node-3)
[root@node-1 pki]# WORKER_IPS=(172.16.1.22 172.16.1.23)
# 批量生成所有worker节点的证书配置
[root@node-1 pki]# for ((i=0;i<${#WORKERS[@]};i++)); do
cat > ${WORKERS[$i]}-csr.json <<EOF
{
"CN": "system:node:${WORKERS[$i]}",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"L": "Beijing",
"O": "system:nodes",
"OU": "seven",
"ST": "Beijing"
}
]
}
EOF
cfssl gencert \
-ca=ca.pem \
-ca-key=ca-key.pem \
-config=ca-config.json \
-hostname=${WORKERS[$i]},${WORKER_IPS[$i]} \
-profile=kubernetes \
${WORKERS[$i]}-csr.json | cfssljson -bare ${WORKERS[$i]}
done
2022/11/03 15:19:29 [INFO] generate received request
2022/11/03 15:19:29 [INFO] received CSR
2022/11/03 15:19:29 [INFO] generating key: rsa-2048
2022/11/03 15:19:30 [INFO] encoded CSR
2022/11/03 15:19:30 [INFO] signed certificate with serial number XX
2022/11/03 15:19:30 [INFO] generate received request
2022/11/03 15:19:30 [INFO] received CSR
2022/11/03 15:19:30 [INFO] generating key: rsa-2048
2022/11/03 15:19:30 [INFO] encoded CSR
2022/11/03 15:19:30 [INFO] signed certificate with serial number XX
[root@node-1 pki]# ll node*
-rw-r--r-- 1 root root 1021 Nov 3 15:19 node-2.csr
-rw-r--r-- 1 root root 224 Nov 3 15:19 node-2-csr.json
-rw------- 1 root root 1679 Nov 3 15:19 node-2-key.pem
-rw-r--r-- 1 root root 1456 Nov 3 15:19 node-2.pem
-rw-r--r-- 1 root root 1021 Nov 3 15:19 node-3.csr
-rw-r--r-- 1 root root 224 Nov 3 15:19 node-3-csr.json
-rw------- 1 root root 1675 Nov 3 15:19 node-3-key.pem
-rw-r--r-- 1 root root 1456 Nov 3 15:19 node-3.pem
组件证书:kube-controller-manager客户端证书
组件证书:kube-controller-manager客户端证书
#kube-controller-manager客户端证书配置文件
[root@node-1 pki]# cat > kube-controller-manager-csr.json <<EOF
{
"CN": "system:kube-controller-manager",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "BeiJing",
"L": "BeiJing",
"O": "system:kube-controller-manager",
"OU": "seven"
}
]
}
EOF
#生成kube-controller-manager客户端证书
[root@node-1 pki]# cfssl gencert \
-ca=ca.pem \
-ca-key=ca-key.pem \
-config=ca-config.json \
-profile=kubernetes \
kube-controller-manager-csr.json | cfssljson -bare kube-controller-manager
2022/11/03 15:21:44 [INFO] generate received request
2022/11/03 15:21:44 [INFO] received CSR
2022/11/03 15:21:44 [INFO] generating key: rsa-2048
2022/11/03 15:21:44 [INFO] encoded CSR
2022/11/03 15:21:44 [INFO] signed certificate with serial number XX
2022/11/03 15:21:44 [WARNING] This certificate lacks a "hosts" field. This makes it unsuitable for
websites. For more information see the Baseline Requirements for the Issuance and Management
of Publicly-Trusted Certificates, v.1.1.6, from the CA/Browser Forum (https://cabforum.org);
specifically, section 10.2.3 ("Information Requirements").
[root@node-1 pki]# ll kube-controller-manager*
-rw-r--r-- 1 root root 1066 Nov 3 15:21 kube-controller-manager.csr
-rw-r--r-- 1 root root 286 Nov 3 15:21 kube-controller-manager-csr.json
-rw------- 1 root root 1679 Nov 3 15:21 kube-controller-manager-key.pem
-rw-r--r-- 1 root root 1464 Nov 3 15:21 kube-controller-manager.pem
组件证书:kube-proxy客户端证书(kube-proxy)
#kube-proxy组件使用
#kube-proxy客户端证书配置文件
[root@node-1 pki]# cat > kube-proxy-csr.json <<EOF
{
"CN": "system:kube-proxy",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "BeiJing",
"L": "BeiJing",
"O": "k8s",
"OU": "seven"
}
]
}
EOF
#生成kube-proxy客户端证书
[root@node-1 pki]# cfssl gencert \
-ca=ca.pem \
-ca-key=ca-key.pem \
-config=ca-config.json \
-profile=kubernetes \
kube-proxy-csr.json | cfssljson -bare kube-proxy
2022/11/03 15:25:26 [INFO] generate received request
2022/11/03 15:25:26 [INFO] received CSR
2022/11/03 15:25:26 [INFO] generating key: rsa-2048
2022/11/03 15:25:26 [INFO] encoded CSR
2022/11/03 15:25:26 [INFO] signed certificate with serial number XX
2022/11/03 15:25:26 [WARNING] This certificate lacks a "hosts" field. This makes it unsuitable for
websites. For more information see the Baseline Requirements for the Issuance and Management
of Publicly-Trusted Certificates, v.1.1.6, from the CA/Browser Forum (https://cabforum.org);
specifically, section 10.2.3 ("Information Requirements").
[root@node-1 pki]# ll kube-proxy*
-rw-r--r-- 1 root root 1009 Nov 3 15:25 kube-proxy.csr
-rw-r--r-- 1 root root 214 Nov 3 15:25 kube-proxy-csr.json
-rw------- 1 root root 1675 Nov 3 15:25 kube-proxy-key.pem
-rw-r--r-- 1 root root 1407 Nov 3 15:25 kube-proxy.pem
组件证书:kube-scheduler客户端证书
#kube-scheduler客户端证书配置文件
[root@node-1 pki]# cat > kube-scheduler-csr.json <<EOF
{
"CN": "system:kube-scheduler",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "BeiJing",
"L": "BeiJing",
"O": "system:kube-scheduler",
"OU": "seven"
}
]
}
EOF
#生成kube-scheduler客户端证书
[root@node-1 pki]# cfssl gencert \
-ca=ca.pem \
-ca-key=ca-key.pem \
-config=ca-config.json \
-profile=kubernetes \
kube-scheduler-csr.json | cfssljson -bare kube-scheduler
2022/11/03 15:30:50 [INFO] generate received request
2022/11/03 15:30:50 [INFO] received CSR
2022/11/03 15:30:50 [INFO] generating key: rsa-2048
2022/11/03 15:30:51 [INFO] encoded CSR
2022/11/03 15:30:51 [INFO] signed certificate with serial number XX
2022/11/03 15:30:51 [WARNING] This certificate lacks a "hosts" field. This makes it unsuitable for
websites. For more information see the Baseline Requirements for the Issuance and Management
of Publicly-Trusted Certificates, v.1.1.6, from the CA/Browser Forum (https://cabforum.org);
specifically, section 10.2.3 ("Information Requirements").
[root@node-1 pki]# ll kube-scheduler*
-rw-r--r-- 1 root root 1041 Nov 3 15:30 kube-scheduler.csr
-rw-r--r-- 1 root root 268 Nov 3 15:30 kube-scheduler-csr.json
-rw------- 1 root root 1675 Nov 3 15:30 kube-scheduler-key.pem
-rw-r--r-- 1 root root 1440 Nov 3 15:30 kube-scheduler.pem
组件证书:kube-apiserver服务端证书
#kube-apiserver服务端证书配置文件
[root@node-1 pki]# cat > kubernetes-csr.json <<EOF
{
"CN": "kubernetes",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "BeiJing",
"L": "BeiJing",
"O": "k8s",
"OU": "seven"
}
]
}
EOF
#生成kube-apiserver服务端证书
#服务端证书与客户端略有不同,当客户端访问服务端时,客户端需要通过一个名字或者一个ip去访问服务端,所以服务端证书必须要包含客户端所访问的名字或ip,用于客户端验证。
所以要把apiserver所有的访问方式全都列出来。有些apiserver可以通过虚拟SERVICE IP来访问。
# apiserver的service ip地址(一般是svc网段的第一个ip)
#(定义一个虚拟SERVICE IP/SVC_IP,这边定义为SVC_IP列表的第一个IP,
如果10.233这个网段跟现有网段有冲突的话,可以换成一个标准的内网IP,最后是.0.1就OK了。
没有冲突的话,那么跟作者的写成一致的即可,以免产生混乱。)
#这个一定要加!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
[root@node-1 pki]# KUBERNETES_SVC_IP=10.233.0.1
# 所有的master内网ip,逗号分隔(云环境可以加上master公网ip以便支持公网ip访问)
(这里只的是服务器的所有可以访问的公网/内网的IP吧。所有worker的也都加上,以免以后worker变成master。
按现有自己虚拟机的NAT模式来说,只配置10网段就可以,因为需要外网访问。多加几台也没关系,以免后续再修改了。)
[root@node-1 pki]# MASTER_IPS=172.16.1.21,172.16.1.22,172.16.1.23,10.0.0.21,10.0.0.22,10.0.0.23
# 生成证书
[root@node-1 pki]# cfssl gencert \
-ca=ca.pem \
-ca-key=ca-key.pem \
-config=ca-config.json \
#可以发现这里不仅有定义的IP变量,还有变量后面一系列的IP和名称,表示通过变量后面的IP和名称都可以访问到K8S。
-hostname=${KUBERNETES_SVC_IP},${MASTER_IPS},127.0.0.1,kubernetes,kubernetes.default,kubernetes.default.svc,kubernetes.default.svc.cluster,kubernetes.svc.cluster.local \
-profile=kubernetes \
kubernetes-csr.json | cfssljson -bare kubernetes
2022/11/03 15:39:54 [INFO] generate received request
2022/11/03 15:39:54 [INFO] received CSR
2022/11/03 15:39:54 [INFO] generating key: rsa-2048
2022/11/03 15:39:55 [INFO] encoded CSR
2022/11/03 15:39:55 [INFO] signed certificate with serial number 196962819208842629453468949172510499986538757616
[root@node-1 pki]# ll kubernetes*
-rw-r--r-- 1 root root 1001 Nov 3 15:39 kubernetes.csr
-rw-r--r-- 1 root root 207 Nov 3 15:39 kubernetes-csr.json
-rw------- 1 root root 1679 Nov 3 15:39 kubernetes-key.pem
-rw-r--r-- 1 root root 1647 Nov 3 15:39 kubernetes.pem
组件证书:Service Account证书
#配置文件
[root@node-1 pki]# cat > service-account-csr.json <<EOF
{
"CN": "service-accounts",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "BeiJing",
"L": "BeiJing",
"O": "k8s",
"OU": "seven"
}
]
}
EOF
#生成证书
[root@node-1 pki]# cfssl gencert \
-ca=ca.pem \
-ca-key=ca-key.pem \
-config=ca-config.json \
-profile=kubernetes \
service-account-csr.json | cfssljson -bare service-account
2022/11/03 15:48:04 [INFO] generate received request
2022/11/03 15:48:04 [INFO] received CSR
2022/11/03 15:48:04 [INFO] generating key: rsa-2048
2022/11/03 15:48:04 [INFO] encoded CSR
2022/11/03 15:48:04 [INFO] signed certificate with serial number XX
2022/11/03 15:48:04 [WARNING] This certificate lacks a "hosts" field. This makes it unsuitable for
websites. For more information see the Baseline Requirements for the Issuance and Management
of Publicly-Trusted Certificates, v.1.1.6, from the CA/Browser Forum (https://cabforum.org);
specifically, section 10.2.3 ("Information Requirements").
[root@node-1 pki]# ll service-account*
-rw-r--r-- 1 root root 1009 Nov 3 15:48 service-account.csr
-rw-r--r-- 1 root root 213 Nov 3 15:47 service-account-csr.json
-rw------- 1 root root 1675 Nov 3 15:48 service-account-key.pem
-rw-r--r-- 1 root root 1407 Nov 3 15:48 service-account.pem
组件证书:proxy-client 证书
(本身并没有什么特殊的,通过CA去签发。
但是用处跟上面的都不同,这个证书是给 aggregator 的API SERVER去使用的,是一个聚合的API SERVER,
简单来说,通过一个证书去访问API SERVER的时候,API SERVER要把我们的请求转发给一个聚合的API SERVER,
这个时候,API SERVER会拿这个证书去访问别人,就相当于一个链路比较长,A传给B,B传给C,用了不同的证书。
这个就是专门用于聚合API的,聚合API主要是为了方便用户开发自己的API SERVER,不用修改K8S的源码,这样一来,跟API SERVER进行解耦,方便用户去使用一些实现的特性。
这里的知识点不太好理解,暂时选择性忽略,先知道使用这个证书即可。)
#配置文件
[root@node-1 pki]# cat > proxy-client-csr.json <<EOF
{
"CN": "aggregator",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "BeiJing",
"L": "BeiJing",
"O": "k8s",
"OU": "seven"
}
]
}
EOF
#生成证书
[root@node-1 pki]# cfssl gencert \
-ca=ca.pem \
-ca-key=ca-key.pem \
-config=ca-config.json \
-profile=kubernetes \
proxy-client-csr.json | cfssljson -bare proxy-client
2022/11/03 15:53:08 [INFO] generate received request
2022/11/03 15:53:08 [INFO] received CSR
2022/11/03 15:53:08 [INFO] generating key: rsa-2048
2022/11/03 15:53:08 [INFO] encoded CSR
2022/11/03 15:53:08 [INFO] signed certificate with serial number XX
2022/11/03 15:53:08 [WARNING] This certificate lacks a "hosts" field. This makes it unsuitable for
websites. For more information see the Baseline Requirements for the Issuance and Management
of Publicly-Trusted Certificates, v.1.1.6, from the CA/Browser Forum (https://cabforum.org);
specifically, section 10.2.3 ("Information Requirements").
[root@node-1 pki]# ll proxy-client*
-rw-r--r-- 1 root root 1001 Nov 3 15:53 proxy-client.csr
-rw-r--r-- 1 root root 207 Nov 3 15:53 proxy-client-csr.json
-rw------- 1 root root 1675 Nov 3 15:53 proxy-client-key.pem
-rw-r--r-- 1 root root 1399 Nov 3 15:53 proxy-client.pem
分发:客户端、服务端证书
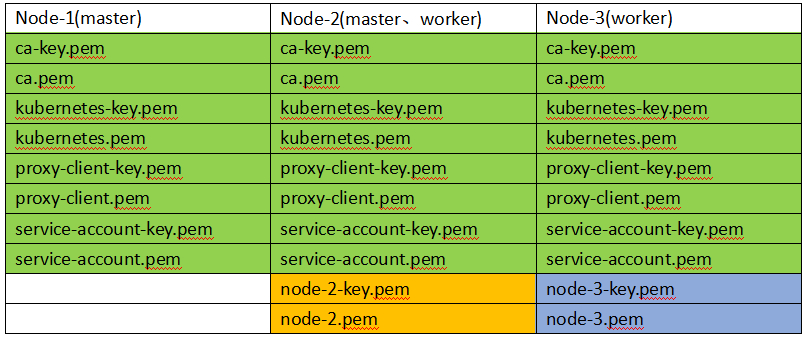
#1、分发worker节点需要的证书和私钥(根证书和每个节点的证书及密钥)
[root@node-1 pki]# WORKERS=(node-2 node-3)
[root@node-1 pki]# for instance in ${WORKERS[@]}; do
scp ca.pem ${instance}-key.pem ${instance}.pem root@${instance}:~/
done
#核实结果
[root@node-2 ~]# ll ~/*.pem
-rw-r--r-- 1 root root 1367 Nov 3 16:09 /root/ca.pem
-rw------- 1 root root 1679 Nov 3 16:09 /root/node-2-key.pem
-rw-r--r-- 1 root root 1456 Nov 3 16:09 /root/node-2.pem
[root@node-3 ~]# ll ~/*.pem
-rw-r--r-- 1 root root 1367 Nov 3 16:09 /root/ca.pem
-rw------- 1 root root 1675 Nov 3 16:09 /root/node-3-key.pem
-rw-r--r-- 1 root root 1456 Nov 3 16:09 /root/node-3.pem
#2、分发master节点和ETCD节点需要的证书和私钥(几乎是所有的证书了)
注意:由于下面分发的证书即包含了etcd的证书也包含了k8s主节点的证书。
所以 MASTER_IPS 中必须包含所有 master 节点以及 etcd 节点。如果没有包含所有etcd节点的证书,需要重新定义,逗号分隔。
#这个 MASTER_IPS 在上面章节设置过了同一台机器的内外网IP,分发文件时会有覆盖的情况),所以这里重新声明一次变量。
[root@node-1 pki]# MASTER_IPS=172.16.1.21,172.16.1.22,172.16.1.23
[root@node-1 pki]# OIFS=$IFS
IFS=','
for instance in ${MASTER_IPS}; do
scp ca.pem ca-key.pem kubernetes-key.pem kubernetes.pem \
service-account-key.pem service-account.pem proxy-client.pem proxy-client-key.pem root@${instance}:~/
done
IFS=$OIFS
#核实结果
[root@node-1 ~]# ll ca.pem ca-key.pem kubernetes-key.pem kubernetes.pem service-account-key.pem service-account.pem proxy-client.pem proxy-client-key.pem ~/.
-rw------- 1 root root 1679 Nov 3 16:11 ca-key.pem
-rw-r--r-- 1 root root 1367 Nov 3 16:11 ca.pem
-rw------- 1 root root 1679 Nov 3 16:11 kubernetes-key.pem
-rw-r--r-- 1 root root 1647 Nov 3 16:11 kubernetes.pem
-rw------- 1 root root 1675 Nov 3 16:11 proxy-client-key.pem
-rw-r--r-- 1 root root 1399 Nov 3 16:11 proxy-client.pem
-rw------- 1 root root 1675 Nov 3 16:11 service-account-key.pem
-rw-r--r-- 1 root root 1407 Nov 3 16:11 service-account.pem
[root@node-2 ~]# ll ca.pem ca-key.pem kubernetes-key.pem kubernetes.pem service-account-key.pem service-account.pem proxy-client.pem proxy-client-key.pem ~/.
-rw------- 1 root root 1679 Nov 3 16:11 ca-key.pem
-rw-r--r-- 1 root root 1367 Nov 3 16:11 ca.pem
-rw------- 1 root root 1679 Nov 3 16:11 kubernetes-key.pem
-rw-r--r-- 1 root root 1647 Nov 3 16:11 kubernetes.pem
-rw------- 1 root root 1675 Nov 3 16:11 proxy-client-key.pem
-rw-r--r-- 1 root root 1399 Nov 3 16:11 proxy-client.pem
-rw------- 1 root root 1675 Nov 3 16:11 service-account-key.pem
-rw-r--r-- 1 root root 1407 Nov 3 16:11 service-account.pem
[root@node-3 ~]# ll ca.pem ca-key.pem kubernetes-key.pem kubernetes.pem service-account-key.pem service-account.pem proxy-client.pem proxy-client-key.pem ~/.
-rw------- 1 root root 1679 Nov 3 16:11 ca-key.pem
-rw-r--r-- 1 root root 1367 Nov 3 16:11 ca.pem
-rw------- 1 root root 1679 Nov 3 16:11 kubernetes-key.pem
-rw-r--r-- 1 root root 1647 Nov 3 16:11 kubernetes.pem
-rw------- 1 root root 1675 Nov 3 16:11 proxy-client-key.pem
-rw-r--r-- 1 root root 1399 Nov 3 16:11 proxy-client.pem
-rw------- 1 root root 1675 Nov 3 16:11 service-account-key.pem
-rw-r--r-- 1 root root 1407 Nov 3 16:11 service-account.pem
标题:Kubernetes(五)kubernetes-the-hard-way方式(5.2)生成证书
作者:yazong
地址:https://blog.llyweb.com/articles/2022/11/03/1667464538685.html